SharePoint Online offers a nifty security feature known as “app-enforced restrictions”. In this article, I will briefly describe the feature and show you how to enable it. I will also point out why there is a need to be aware of what is happening in the background in case turning it on causes issues for you elsewhere in the M365 platform.
App-enforced restrictions are all about ensuring your corporate data doesn’t unintentionally end up on devices over which you have no control. Once enabled, the feature will prevent your users from downloading, printing or syncing SharePoint Online data from your tenant on unmanaged devices. In this context, an unmanaged device is one that is either not considered compliant by Intune, or is not hybrid Azure AD domain-joined.
Here’s how to enable it. Open up the SharePoint Online Admin Center with an account that has the SharePoint Administrator role. From the left hand pane, expand the Policies option and then select Access control. In the Access control view, select Unmanaged devices (the first option).
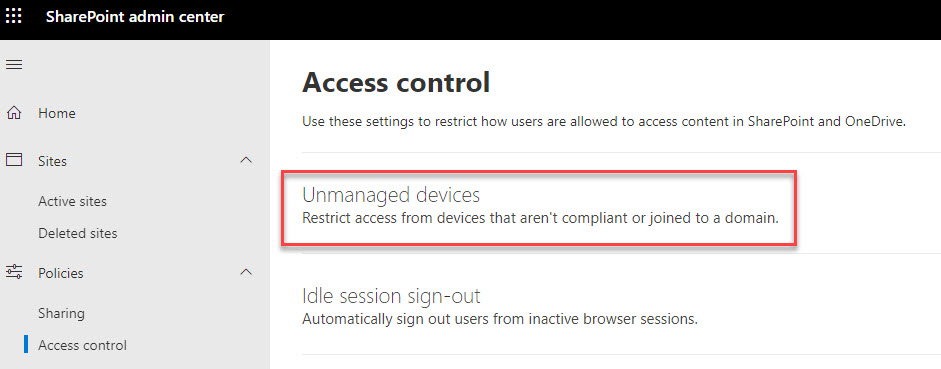
The default setting is to allow full access from desktop apps, mobile apps and web. To apply limited, web-only access, select the middle option as shown in the screenshot below.
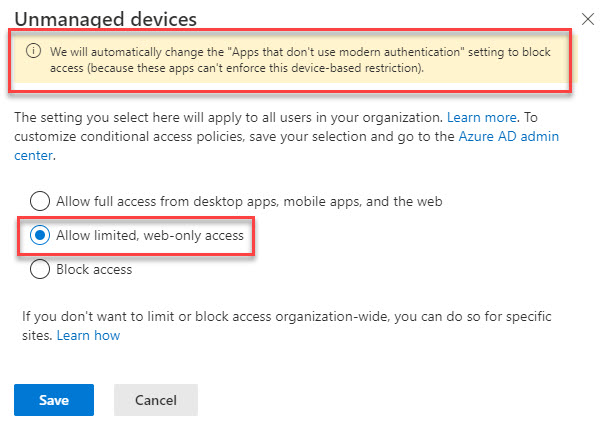
Note the warning at the top about “Apps that don’t use modern authentication”. In my case, this SharePoint Online setting (also under the Access Control section) wasn’t updated to “Block” as expected. Your mileage may vary.
Now that you have enabled the feature, how do you know it’s working as intended? If you go to an unmanaged device and open up SharePoint Online from a browser, then you should see the warning banner shown below.
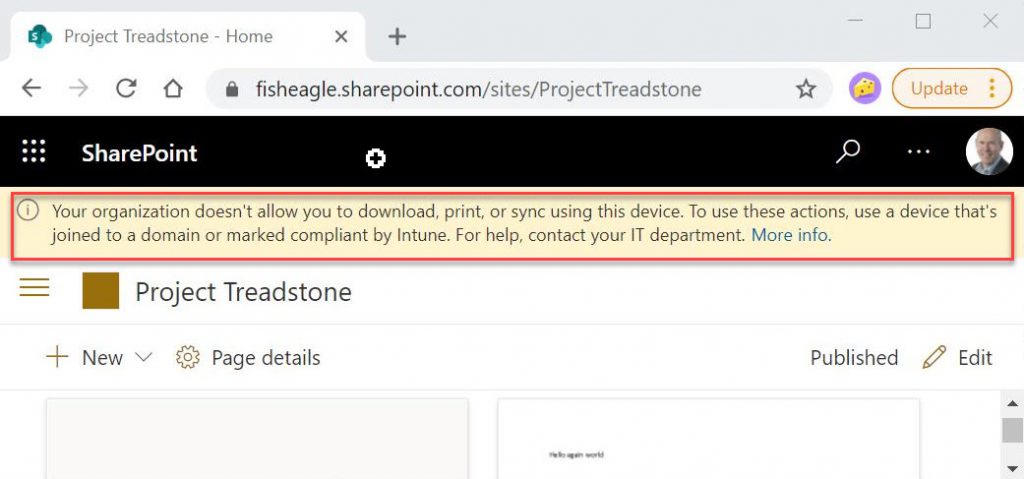
As the warning suggests, you will be able to view files, but not download them to the unmanaged device. You will also be unable print or sync (to OneDrive).
So, that’s it then. Nothing more to do other than a pat on the back and a trip to the pub for a swift celebratory drink? Possibly. But you might equally have some irate users outside your door with pitchforks and flaming torches wanting your blood for breaking their access to various platform tools. Why? It’s because of the way in which two new Azure AD Conditional Access policies are created automatically and turned on when enabling app-enforced restrictions. Frankly, it’s not done with much finesse. The two policies created are shown below.
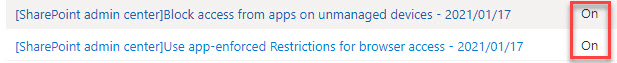
The first policy allows access to SharePoint online from mobile apps and desktop clients, but only if from devices that are marked as compliant by Intune or that are hybrid AAD domain-joined.
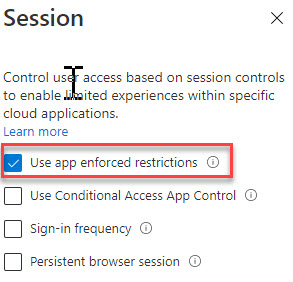
The second policy uses a session control to instruct SharePoint Online to apply app-enforced restrictions for connections from a browser (see screenshot below).
I find these CA policies problematic for a number of reasons:
- There is no notification to the administrator when enabling app-enforced restrictions that these two CA policies will be created. None!
- The policies are created and turned “On” by default. Yes, the app-enforced restriction feature was created before CA “Report-only” mode was introduced, but this would be a much better option to allow admins to evaluate the impact prior to turning the CA policies on.
- The policies can have a negative impact on other types of access that rely on SharePoint Online. For example, you could have Teams or OneDrive BYOD users that would immediately stop working after the app-enforced restriction is enabled, because these both leverage SharePoint Online at the back end.
- If you toggle app-enforced restrictions off and on again, it will create a brand new pair of CA policies with a different date stamp…without removing any previously created policies! It’s just not very intelligent.
In my opinion, it would be much more helpful if the admin were given more information about the CA policies and their potential impact when enabling app-enforced restrictions. Leave it up to the admin to decide how and when to implement the required CA policy settings.
In this blog article, I’ve briefly explained the usefulness of the app-enforced restrictions feature, how to enable it, how to confirm it’s working, and what potential gotchas to watch out in the CA policy space. If you would like to hear more about either this feature or about Conditional Access policies, please leave a comment. Thanks!

Is there any other option that allow an external user who is using an unmanaged device to download and print a file from SharePoint?