When something runs in Audit mode, you generally expect it not to block anything, right? I recently found an anomaly with Microsoft Defender Application Control runing in Audit mode causing .hta files not to open. An HTML Application (HTA) is a Microsoft Windows program whose source code consists of HTML, Dynamic HTML, and one or more scripting languages supported by Internet Explorer, such as VBScript or JScript. Not only does MDAC block .hta files, it doesn’t log anything to indicate that it has done so in the codeintegrity operational event log (which is where you would expect to learn about what has been blocked from running).
You should be able to reproduce this easily for yourself by following the steps below.
Firstly, confirm that you are able to open .hta files using the default application (mshta.exe). If you need a simple test file, you can find one here.

Create a new Endpoint Protection profile in Intune with the following settings.
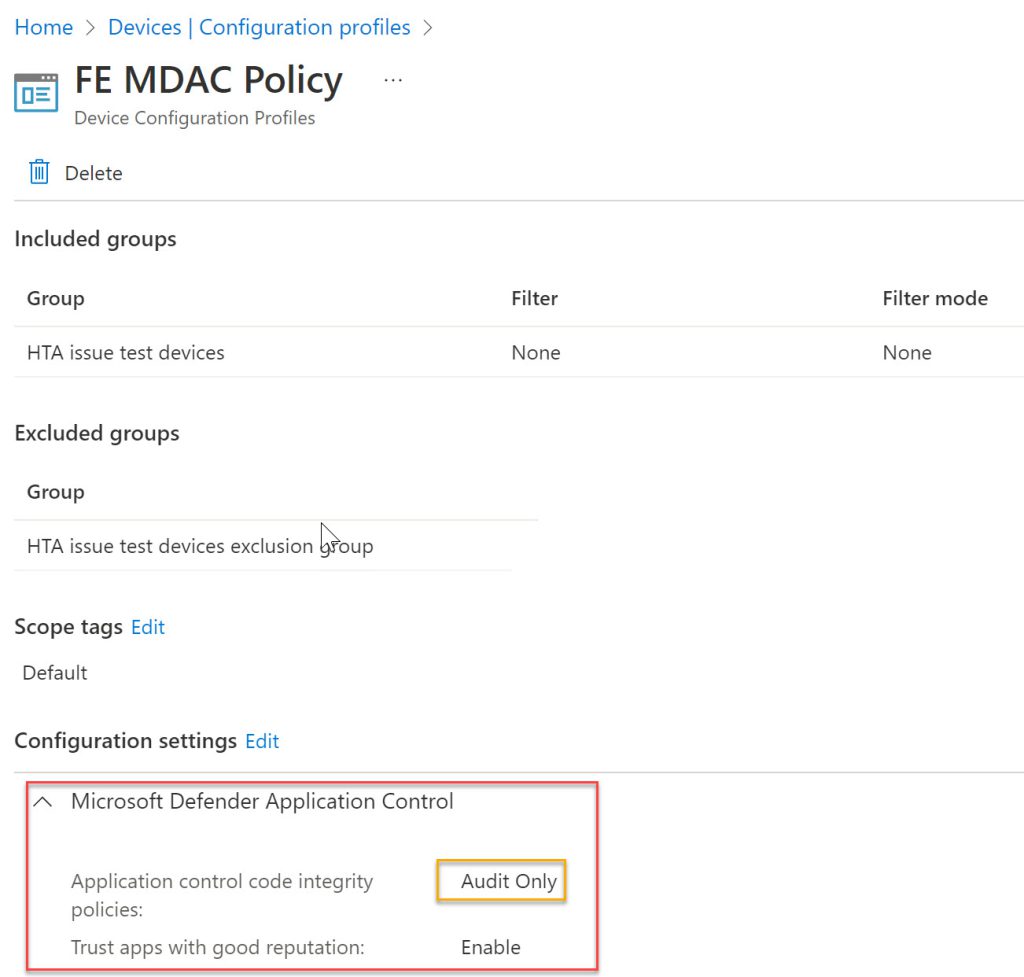
Assign the profile to a group containing your test device(s)
Sync the device to pick up the profile settings. You should see a warning that the device will restart in 10 minutes.
After the reboot, try to open the .hta file again. You will be blocked with no warning or error. It just won’t open.
Look in the codeintegrity operational log. You won’t see anything about the file being blocked.
If you drop your test device out of the assignment group and re-sync to pick up the changes, you will see the 10 minute warning again. After the restart, your ability to open .hta files will be back.
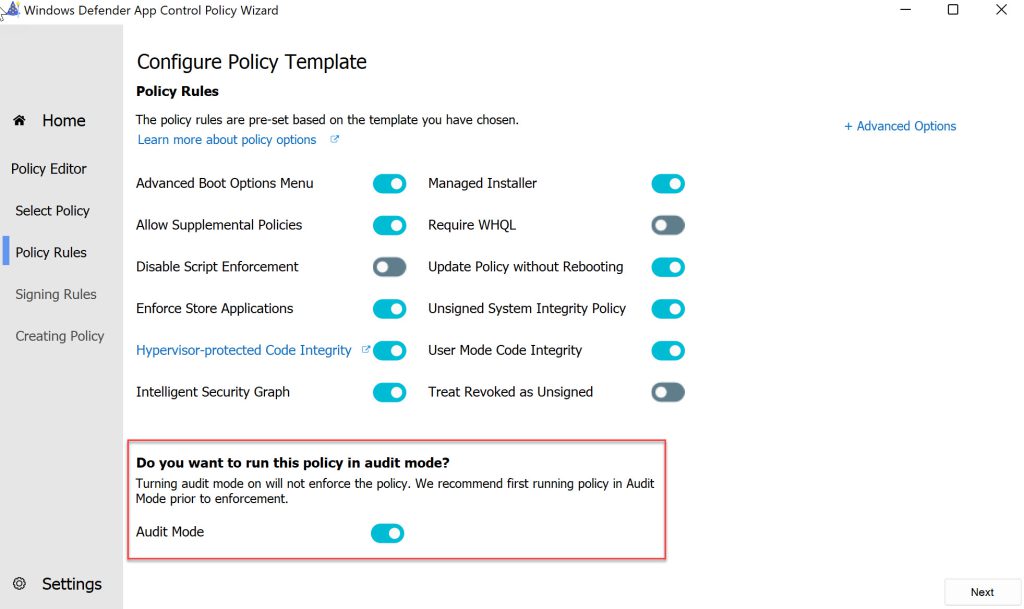
Note that the same behaviour occurs with profiles that have been created using the Windows Defender Application Control Wizard and configured to run in audit mode.
So, there you have it! Not a great discovery and a tricky one to troubleshoot without any pop-up warnings or event log entries to work with. Hopefully Microsoft will sort this out in the near future.

I am also seeing the same behaviour in my environment. We still want to run WDAC in audit mode, did you find a way to fix this other than disable the policy?